Signs of Intrusions Include Which of the Following
3 Monitor and Inspect Network Activities. Either individuals or members of an organized crime group with a goal of financial award.
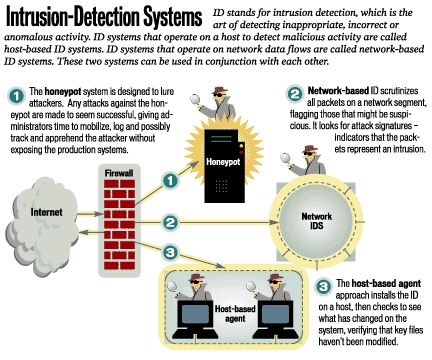
Intrusion Detection Computerworld
Network and analyzing them for signs of possible incidents which are violations or imminent.

. Threats of violation of computer security policies acceptable use policies or standard security. Upon discovering unauthorized unexpected or suspicious activity you may need to 1 initiate your intrusion response procedures as described in Chapter 7 and 2 determine if the activity should be reflected in your characterization baseline alerting or other data collection mechanisms. Meet in underground forums to coordinate attacks.
5 Inspect Files and Directories for Unexpected Changes. Intrusion Detection and Prevention Systems. One pupil larger than the other.
A system alarm or similar indication from an intrusion detection tool. Choose all that apply Question 2 options. Call 9-1-1 right away or take your child or teen to the emergency department if he or she has one or more of the following danger signs after a bump blow or jolt to the head or body.
Facebook Google Dropbox Salesforce Mobile Physical Based Attacks include choose all that apply. To achieve this their activities may include identity theft theft of financial credentials corporate espionage data theft or data ransoming. System Crashes Strange Processes Slow Performance Missing Logs Some of the Characteristics of Cloud Computing services include select all that apply.
Suspicious entries in system or network accounting eg a UNIX user obtains privileged access without using authorized methods. They may attempt to breach your networks perimeter defenses from remote locations or try to physically infiltrate your organization to access information resources. Dangerous Signs Symptoms of a Concussion.
Intrusion detection is the process of monitoring the events occurring in a computer system or. 2 Ensure That the Software Used to Examine Systems Has Not Been Compromised. Detecting Signs of Intrusion.
Exceptionally slow network activity disconnection from network servi ce or unusual network traffic. Choose all that apply System Crashes Slow Performance Missing Logs Strange Processes Examples of companies that offer Cloud Computing services include select all that apply. Intruders make use of systems they have compromised to launch attacks against othersIf one of your systems is used in this wayyou may be held liable for not exercising adequate due care with respect to security.
Signs of Intrusions include which of the following. What are signs of a network intrusion. Intruders are always looking for new ways to break into networked computer systems.
Detecting Signs of Intrusion. Signs that your system may be compromised include. Choose all that apply a missing files b repeated service probes c sudden influx of data d file size modifications.
Lost business opportunities coupled with loss of reputation. 4 Monitor and Inspect System Activities. Signature detection Signs of Intrusions include which of the following.
69 Take Appropriate Actions. Resource Pooling Distributed Storage Measured Services Virtualization Technology.

Gdpr Map Step 3 Protect 022818 01 1 Png 1 275 3 547 Pixeles Cybersecurity Infographic General Data Protection Regulation Gdpr Compliance

Structural And Lithological Controls On The Architecture Of Igneous Intrusions Examples From The Nw Australian Shelf Earthdoc

3 Top Iot Security Architectures And How To Fix Them Security Architecture Iot Cyber Security Awareness

Geological Society Igneous Intrusions

Pin On 2019 Archive Of Geology And Ocean Sciences News Headlines Published In Tellus

The Protection Of The Cctv Camera Is No Longer As Novel As It Used To Be In Reality It Is Very Ch Cctv Camera Cctv Security Systems Security Cameras For Home

Powerpoint Law Of Superposition Geology Teaching Earth And Space Science 8th Grade Science

Metamorphic Facies And Plate Tectonics Also Ophiolite Sequence Earth S Mantle Earth And Space Science Solar Energy

Intrusion An Overview Sciencedirect Topics
Intrusion Detection Systems And Local Area Networks Download Scientific Diagram

Infographic Design For A Security Privacy Software Company Data Loss Prevention Data Loss Prevention
What Are Computer Firewall Intrusion Detection Systems And Intrusion Prevention Systems Quora

Intrusion Detection Systems And Local Area Networks Download Scientific Diagram
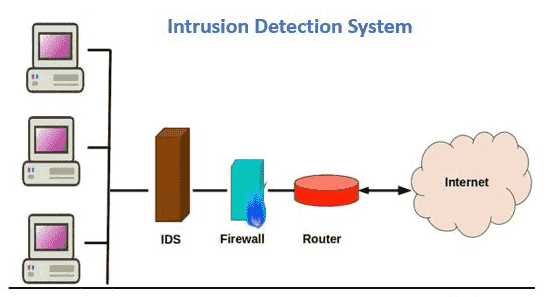
What Is An Intrusion Detection System Ids Ids Security 2022

Overall Framework Of Network Intrusion Detection Model Download Scientific Diagram

Hybrid Intrusion Detection System Based On Ensemble Of C5 And One Class Download Scientific Diagram



Comments
Post a Comment